Bad Rabbit Ransomware Attack – What is it and how to prevent it
With the memory of WannaCry and NotPetya still fresh on our minds, the Bad Rabbit ransomware is the 3rd major attack of it’s kind in 2017. First discovered on 24 October, it appears to be a modified version of the NotPetya worm which largely affected Ukrainian companies.
As reported by BleepingComputer, several security firms have already revealed evidence showing a link between the Bad Rabbit ransomware and the NotPetya ransomware. This time around though, the cyber-espionage group named Telebots are spreading the ransomware via fake Adobe Flash Player updates as opposed to exploiting the NSA’s EternalBlue vulnerability found in the NotPetya attack.
In retrospect, Bad Rabbit actually is a little harder to execute as it requires the victim to grant administrative access to install the malicious codes which is pretending to be an Adobe Flash installer.
Who Has Been Infected
According to cybersecurity company Group-IB, Bad Rabbit has mainly affected Russia and Ukraine which compromised the Kiev metro, the Ministry of Infrastructure and the Odessa International Airport, as well as a number of state organisations in the Russian Federation.
While lesser incidents are reported in Turkey, Germany, Bulgaria, Japan, Poland, South Korea and the United States. In fact, the US-CERT has already issued an alert regarding the attack including a strong discouragement from paying the ransom.
Infected Ground Zero
Infection first took place on legitimate Russian based websites, amongst a growing list of other compromised sites such as:
http://www.fontanka[.]ru
http://argumenti[.]ru
http://argumentiru[.]com
Note: The brackets [] are added to prevent any of our readers from accidentally clicking them.
How Do I Know If I’m Infected
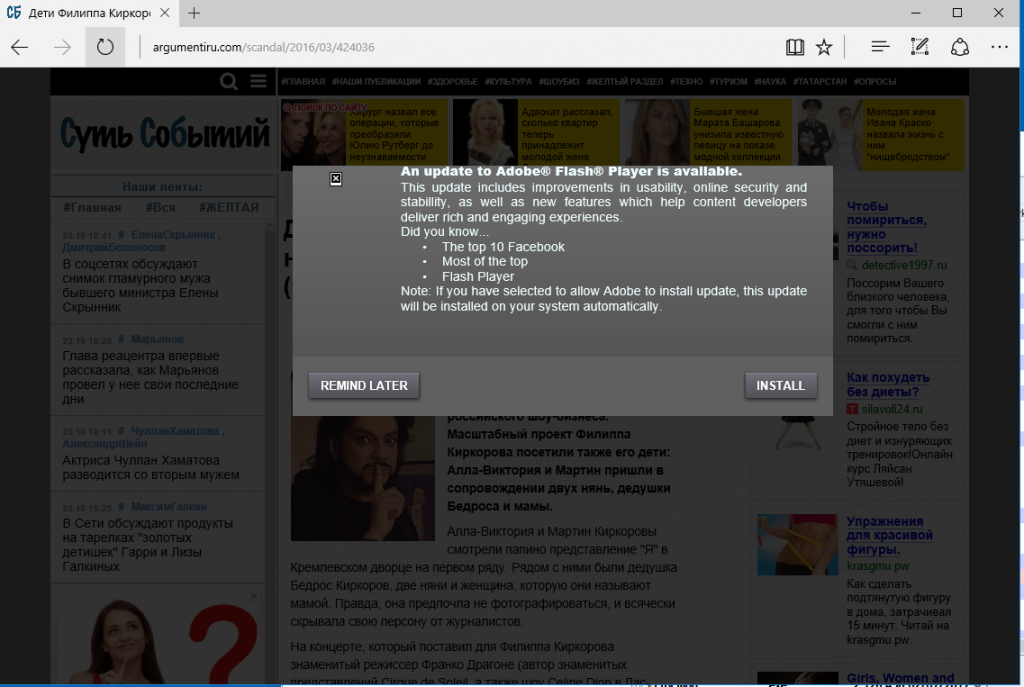
In order for you to be infected by the ransomware, you must’d first landed on a compromised site. In which case, a popup asking you to download an update for Adobe Flash Player is shown on the website’s page.
Bad Rabbit Infected Site – you’ll see this popup requesting installation of a fake Adobe Flash Player update.
If you clicked on the Install button, a download of the executable ransomware is initiated. Once you’ve authorised the executable to be installed, all of your computer files will be encrypted and the note below will be shown.
Bad Rabbit Ransom Payment Prompt – you’ll see this screen if you’re infected.
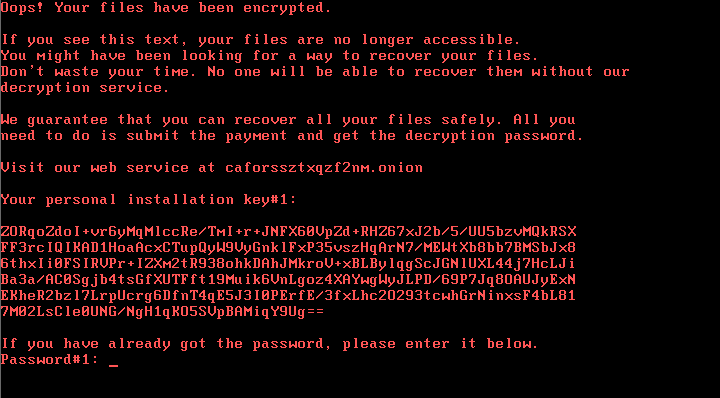
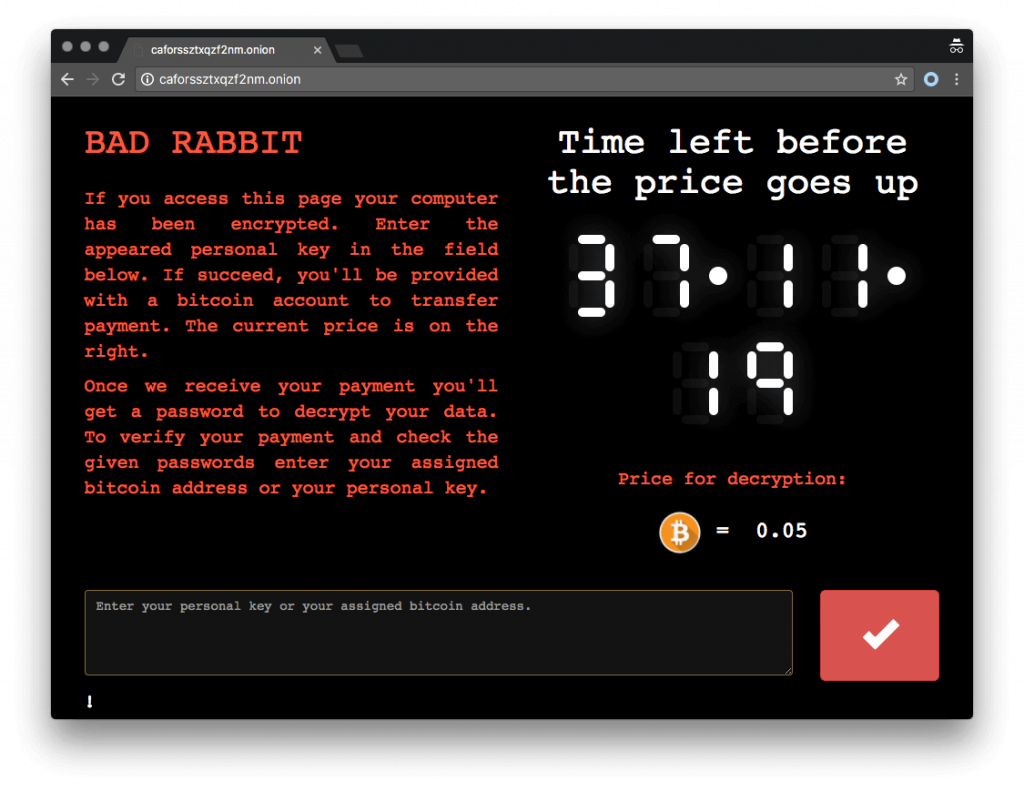
It’ll request you to visit the website caforssztxqzf2nm[.]onion to proceed with a payment of 0.05 Bitcoin (£217 at the time of writing). However, you’ll also notice that the attackers had included a 40-hour timer before the price starts going up if payment has not been received.
Bad Rabbit Payment Page – you’ll be redirected to this website.
Which Systems Are Affected?
Bad Rabbit requires Microsoft executables to run it’s ransomware attack, so it’s currently affecting only Microsoft Windows computers.
How To Protect Myself From Bad Rabbit
Vaccination for the Ukraine round 2? Wanna stop #badrabbit?
Create a file called c:\windows\infpub.dat and remove all write permissions for it. This should keep the malware from encrypting. Testing it now… pic.twitter.com/3MSSH8WKPb— Amit Serper (@0xAmit) October 24, 2017
Security researcher, Amit Serper and Mike Lacovacci of Cybereason has developed a vaccine to prevent your computer from getting infected. Following an early tweet on 25 October, @0xAmit and Cybereason has now published a post with step-by-step instructions for the Bad Rabbit vaccine.
I’m infected with Bad Rabbit. What Can I Do?
Unfortunately if you’re already infected by Bad Rabbit, there is no way to recover files encrypted by the ransomware. However, if you already have a backup of your data or system, you’re in luck. So far the only sure way to remove the ransomware is to,
● Reformat your computer and restore a previously uninfected version of it; OR
● Install a new Windows OS and restore the data files you have backed up.
Should I Pay The Ransom?
We at My Private Network, strongly suggest that you DO NOT adhere to their demands. As reported by TechCrunch, anyone infected is discouraged from paying the ransom. For one, there’s no guarantee you’ll get your data back but more importantly, refusing to pay the ransom discourages future ransomware attacks.
How To Avoid Ransomware?
There’s a very important lesson to learn from all of this, and that’s to always keep your devices up to date and never jailbreak/root your device.
We hope you found this article informative or useful. Help us get the word out and stop the spread of the ransomware by sharing this with your friends and family!