macOS ‘High Sierra’ Root Account Security Fail
The latest version of Apple’s macOS operating system used in their desktop and laptop computers has been discovered to have a gaping security hole allowing anyone with physical or in some cases even network access to effectively ‘own’ the device and access anything on it.
Apple’s Urgent Security Update
Apple have just release a patch – Security Update 2017-001 – and our recommendation is that you install it immediately, seriously, don’t delay, if you are using macOS High Sierra, you MUST fix it now.
The issue arises from the ‘root’ account which is the most powerful account on any UNIX type system, such as macOS. In an effort to be as user friendly as possible, Apple users don’t need to know about this account and although it exists, it should always be disabled and therefore unusable, as it is unusable, there is no need to have a password on it, or so the thinking goes….. With this security issue, it seems that any attempt to use the ‘root’ account actually results in it be re-enabled and as it doesn’t have a password, the attacker gains FULL and ABSOLUTE access to the system.
Fix It Manually
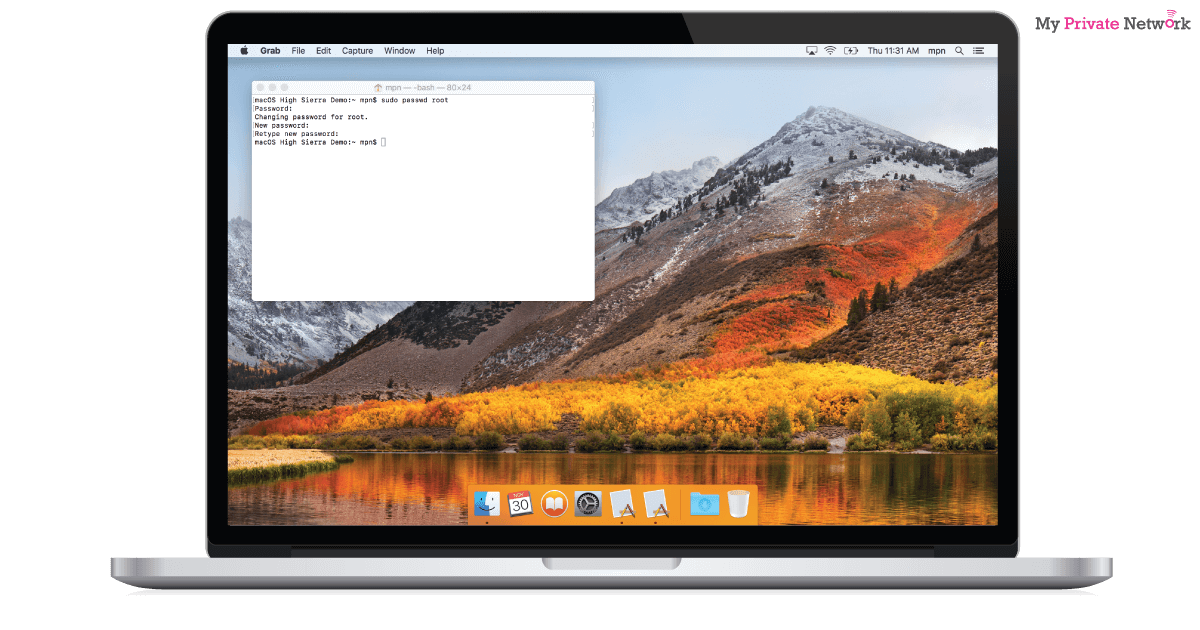
If for any reason you cannot apply the security patch right now, you can fix the issue manually, by simply creating a password for the root user. To do this, open the terminal window and type:
sudo passwd root
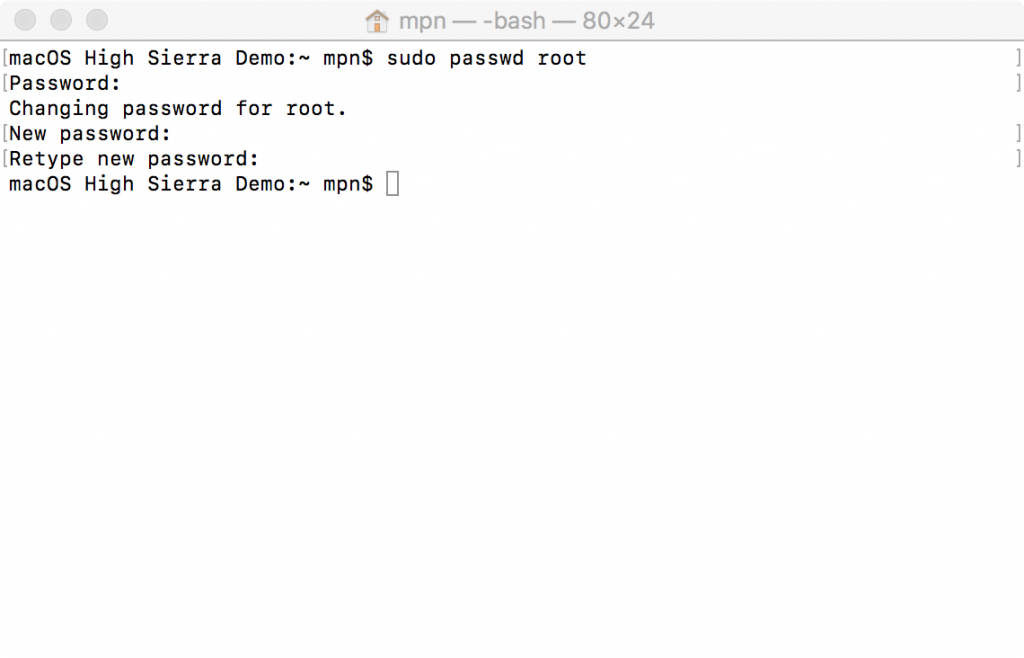
1. You will normally be prompted to enter your own password first to confirm you are legitimate.
2. Then choose a new good, strong password for the root user and enter it twice to confirm – you should remember this password, even though you are unlikely to ever need it again.
Now that you have fixed the problem, perhaps the bigger potential issue is have you already been compromised? How may days or weeks have you been using High Sierra and in what environments? At the time of writing I am not aware of any exploits using this hole, but that doesn’t mean that there aren’t any and given the severity of the issue, you would have no way of knowing if your system has been compromised. And if you were compromised, what might the attacker have got away with, your keychain, your ssh keys, your private certificate keys, your private / work documents, all your saved passwords?
I am sorry to say that I am probably going to spend the rest of the day doing a completely clean and fresh install of High Sierra on my macbookpro and changing all my passwords…….. but then again, I am paranoid.
In the mean time, we hope you’ve found this article informative and would take the necessary steps to protect yourself. Help us get the word out and bring more awareness by sharing this with your friends and family!
If you need any help at all, we’re just an email away at [email protected]. Shoot us an email and our support team will try their best to help you out.