What Is A VPN?
VPN means Virtual Private Network, which is basically a secure connection between two or more devices. It doesn’t physically exist, it is just a temporary encrypted connection between your computer and our servers and as only we have the encryption keys, it is private to us.
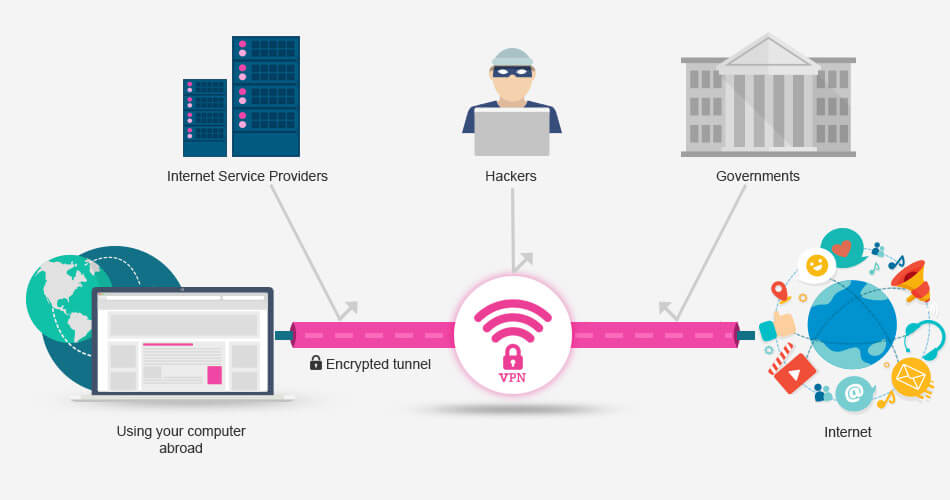
How Does A VPN Work?
When you connect to our service, your computer makes an encrypted connection to one of our secure servers and then sends all of your Internet traffic across that connection. So suppose you are in the United Arab Emirates (for example) and you connect to our server in the United States, the connection between you and our server in the United States will be fully encrypted, and anyone in between cannot see or tell what you are doing on the Internet. This means all hackers, snoopers, ISPs, and third parties can see is an encrypted connection between you and us.
Why Does A VPN Matter?
Well suppose the government of the United Arab Emirates decided that they did not want their people to access Facebook, they can simply firewall all access to facebook.com on the country’s telecommunications equipment and straight away you would not be able to access Facebook.
However, by connecting to our service first, your network traffic would go directly from your computer to one of our secure servers and only then out on the Internet to Facebook. The UAE telecoms people can only see a secure connection to us, they are not able to trace or block your connection to Facebook. Conversely, suppose the board at Twitter (or more likely one of the media companies such as Hulu, ABC, NBC and etc.) decided that their service was only going to be available to U.S based customers, they could simply block access from any location outside of the U.S on their servers.
Again, by using our service and connecting to one of our secure U.S based servers, Twitter would think you are in the U.S and therefore grant you full access. These are fairly generic examples but the principle is simple in which by connecting to our servers, you get to choose which country your computer appears to be in and therefore which rules govern your Internet connection.
What Are VPN Protocols?
A VPN connection utilises different protocol technologies such as PPTP, L2TP, SSL, or IKEv2 to establish a secure connection. Some have been developed since the birth of the Internet, and some are freshly of this decade, but not all are created equally. We support all the main VPN protocols and your account provides you access to use any of them. Here’s a quick breakdown on these protocols below:
| PPTP | L2TP-IPSec | SSL | IKEv2 | |
| Details | Point-to-Point Tunneling Protocol was developed by Microsoft for creating VPN over dial-up networks. It has long been the standard protocol for internal business VPN. PPTP is a VPN protocol only and has a quick implementation due to low computational overhead requirements. |
Layer 2 Tunnel Protocol is a VPN protocol that provides encryption and confidentiality for traffic that passes through it when implemented with the IPsec encryption suite. L2TP over IPsec is as easy and quick to set up as PPTP and is built-in most modern operating systems. |
OpenVPN is an open source VPN solution that uses various technologies, including the OpenSSL library and SSLv3/ TLSv1 encryption protocols. It is highly configurable and can be set to run on any port, although it runs best on a UDP port. It is considered difficult to block as it makes traffic on it impossible to differentiate from traffic using standard HTTPS over SSL. |
Internet Key Exchange version 2 is the newest VPN protocol and based on IPSec tunneling protocol. Jointly developed by Microsoft and Cisco, it is baked into Windows 7+. |
| Security | MPPE – 128bit | AES – 128/256bit | AES – 256bit | AES – 256bit |
| Speed | Highest speed due to basic encryption, but can result in unstable connections. |
L2TP/IPsec has tunneling overhead but still fast due to encryption/decryption efficiency. |
Even on connections with high latency and across great distances it still has great speed, making this the best performing protocol. |
Faster than most VPN protocols. |
| Supported Devices |
All Platforms: Windows, Mac, Linux, iOS, Android, and more |
Most Platforms: Windows, Mac, Linux, iOS, Android, and more |
Most Platforms: Windows, Mac, Linux, iOS, Android, DD-WRT, and more |
Newer Platforms: Windows, Mac, iOS, and Android |
| Pros | • Fast • Very easy setup • Support for all platforms |
• Easy setup • Support on most platforms |
• Very fast • Very secure • Can bypass firewalls • Highly customisable |
• Very fast • Very secure • Very stable • Easy setup |
| Cons | • Stability varies depending on network • Low security level |
• May have slightly slower speeds • Can be problematic on restrictive firewalls |
• Setup may be trickier than other protocols • Not supported on some mobile devices • Requires third party software |
• Not supported on most older platforms |
| Conclusion | A good basic VPN connection, widely supported without any additional software |
An improvement over PPTP and widely supported |
In our humble opinion, the best VPN solution. Although you need to download a bit of software and it is not usually supported on mobile devices. (RECOMMENDED) |
An excellent standard VPN solution, second only to SSL. (RECOMMENDED) |