How to Prevent and Fix WannaCry Ransomware
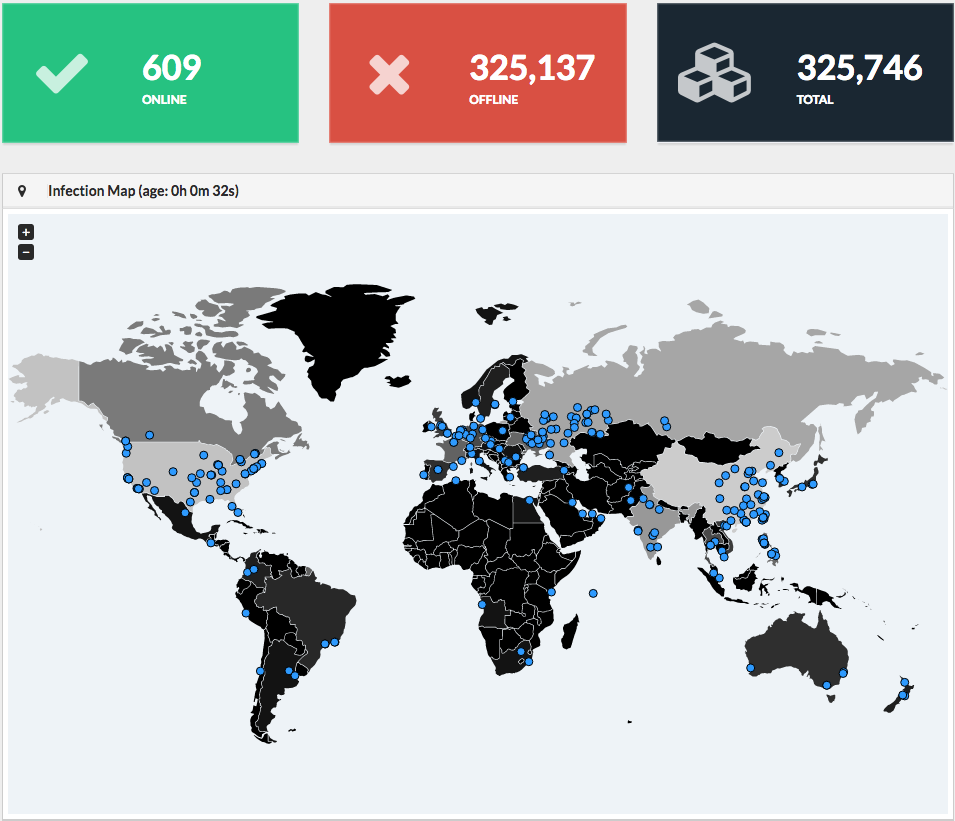
On Friday, 12 May 2017, the world was hit by yet another ransomware attack which infected more than 230,000 computers in over 150 countries. Aptly named “WannaCry“, it is reported that Russia, Ukraine, India, and Taiwan were the worst-hit countries, but is had also reached computer systems in the UK which greatly affected the National Health Service (NHS).
It is important to note that the WannaCry attack only effects versions of the Microsoft Windows operating system that are either obsolete or not up to date. Due to a vulnerability in Microsoft’s Server Message Block (SMB), hackers are able to use the EternalBlue exploit and DoublePulsar backdoor developed by the U.S. National Security Agency (NSA) to spread through local networks and remote hosts. However, many of the infected computers could’ve been avoided by simply updating their Windows version when Microsoft issued a “critical” patch on 14 March 2017. Goes to show that it only takes one weak link to create a huge disaster.
WannaCry Infection Map – MalwareTech.com
How Do I Know If I’m Infected?
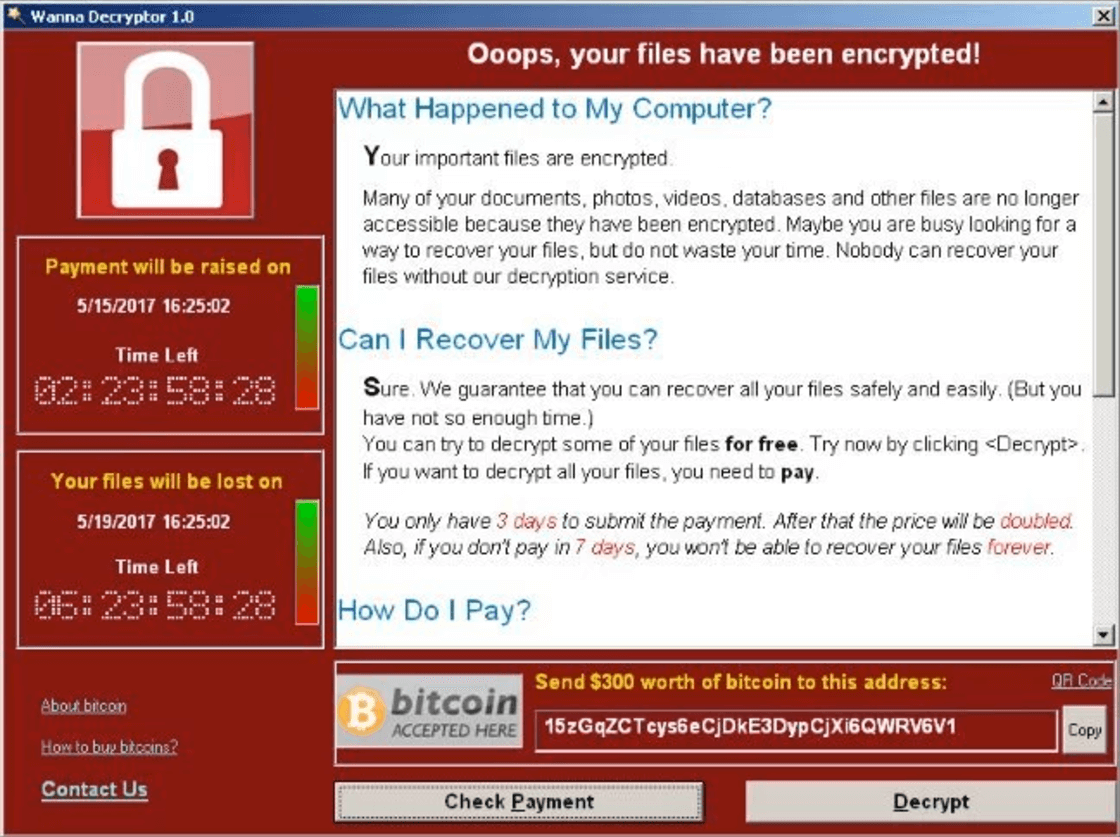
Firstly, WannaCry works by encrypting most or all of the files on your computer. It then demands that a ransom of $300 (£230) be paid in bitcoins to unlock those files. Within three days, the ransom doubles to $600 (£460) if it’s not paid. After seven days without payment, WannaCry will delete all of your files which means there’s little to no chance of recovery.
WannaCry Ransom Payment Prompt – you’ll see this screen if you’re infected.
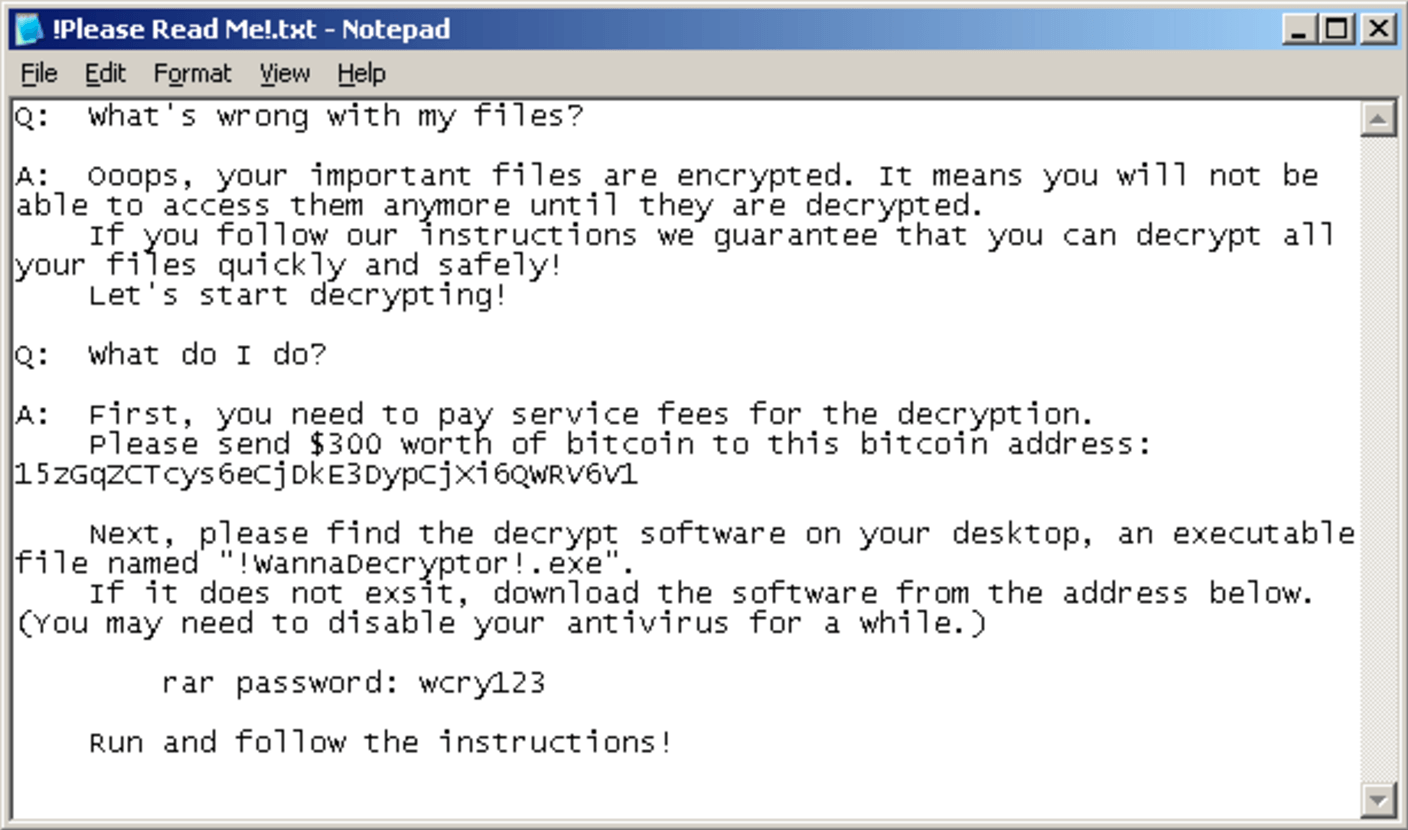
At the same time, WannaCry also installs a text file on the user’s desktop with the following ransom note.
WannaCry Text File – the ransom note.
Which Windows Systems Are Affected?
Any Microsoft Windows systems that are not up to date. See the full list below.
● Windows 10 (1507,1511,1607)
● Windows 8/8.1
● Windows 7
● Windows Vista
● Windows XP
● Windows Server 2008, 2008 R2, 2012, 2012 R2
How To Protect Myself from WannaCry?
It’s very important that you keep your system updated to avoid the risk of being infected.
Follow the steps below and download the latest patch from the official Microsoft Windows library.
Check Your Windows Version
Kindly follow the steps below to check the version of windows you’re running.
1) Press the Windows key + R on your keyboard.
2) In the Run box that appears, type winver and click OK.
3) A windows showing your Windows version will open.
4) Take note of the Windows version and look for the appropriate Windows solution below.
For Windows 10
1) Search and open your Settings.
2) Click on Update and Security.
3) Click the Windows Update tab and it should show you any available updates. If it’s not showing, you can check for the latest update by clicking on Check for Updates.
4) Click Download to start the update process.
For Windows 8
No update available for this version. Kindly upgrade to Windows 8.1.
Temporary Fix: The steps below is to block the vulnerable SMB protocol.
Warning: Blocking the SMB protocol will remove functionality for file sharing, printing over a network, and others. Read more on how SMB protocols are used here.
1) On the Start screen, type PowerShell.
2) Right-click the Windows PowerShell app icon and select Run as administrator.
3) Once PowerShell is launched, type powershell and hit enter.
4) Type or copy/paste the commands below to PowerShell and hit enter after every command,
Press Y and hit Enter when prompted.
Press Y and hit Enter when prompted.
5) Reboot your computer after it’s successful.
For Windows 8.1
Download Windows 8.1 64-bit WannaCry Patch Fix (KB4019215) Here
Download Windows 8.1 32-bit WannaCry Patch Fix (KB4019215) Here
For Windows 7
Download Windows 7 64-bit WannaCry Patch Fix (KB4019264) Here
Download Windows 7 32-bit WannaCry Patch Fix (KB4019264) Here
For Windows Vista
Download Windows Vista 64-bit WannaCry Patch Fix (KB4012598) Here
Download Windows Vista 32-bit WannaCry Patch Fix (KB4012598) Here
For Windows XP
Download Windows XP SP2 64-bit WannaCry Patch Fix (KB4012598) Here
Download Windows XP SP3 32-bit WannaCry Patch Fix (KB4012598) Here
For Windows Server 2008
Download Windows Server 2008 Itanium WannaCry Patch Fix (KB4012598) Here
Download Windows Server 2008 64-bit WannaCry Patch Fix (KB4012598) Here
Download Windows Server 2008 32-bit WannaCry Patch Fix (KB4012598) Here
For Windows Server 2008 R2
Download Windows Server 2008 R2 Itanium WannaCry Patch Fix (KB4012215) Here
Download Windows Server 2008 R2 64-bit WannaCry Patch Fix (KB4012215) Here
For Windows Server 2012
Download Windows Server 2012 64-bit WannaCry Patch Fix (KB4012217) Here
For Windows Server 2012 R2
Download Windows Server 2012 64-bit WannaCry Patch Fix (KB4012216) Here
For the full list of Windows patches available for the WannaCry Ransomware (MS17-010), kindly visit the Microsoft library here.
I’m infected with WannaCry. What Can I Do?
Sadly, there’s currently no confirmed fix for WannaCry if you’ve already been infected. Cybersecurity experts are working hard to find ways to decrypt files on infected computers, but nothing definitive has been available yet.
However, if you have a backup of your data or system, you’re in luck. So far the only sure way to remove the ransomware is to,
● Reformat your computer and restore a previously uninfected version of it; OR
● Install a new Windows OS and restore the data files you have backed up.
Should I Pay The Ransom?
We at My Private Network, strongly suggest that you DO NOT adhere to their demands. As reported by The Guardian via Europol, cybersecurity experts have warned affected users against meeting the hackers’ demands for money.
How To Avoid Ransomware?
It’s no surprise that malicious attacks in recent years have been on the rise as more and more internet-connected devices flood our daily lives. However, it’s been especially prominent on older or rooted systems such as Android devices running OSes 1.5 to 6.0.
There’s a very important lesson to learn from all of this, and that’s to always keep your devices up to date and never jailbreak/root your device.
We hope you found this article informative or useful. Help us get the word out and stop the spread of the ransomware by sharing this with your friends and family!